MT Review Questions
1
General Questions:
a. Both the data link and transport layer provide similar functionality. Why is this not a duplication of effort? (see OSI Seven Layer Model)
b. What functionality does the datalink layer provide?
c. Explain the differences between the network layer and transport layer?
d. A network protocol specifies two things, name and explain them. (see Protocol)
e. Explain the difference between Unicast, Multicast, and Broadcast Transmissions.
Proof
a. The data link layer handles routing based on one hop (think ethernet, while the transport layer handles the traffic end-to-end (multiple hops) and encodes/decodes the higher application layers (think TCP).
b. The datalink layer handles routing to the next device on the interim network (ie: it routes).
c. The network layer handles the traffic end-to-end (ie: says what the IP is for the host address and source address) while the transport layer handles the encoding and error correction once it gets to the device (again, think TCP).
d. A network protocol specifies:
- The format of the data over the network
- The rules of how to interpret data over the network (how it should be routed, for example)
e.
- Unicast Connection: One-to-one (direct connection)
- Multicast Connection: One-to-many (may not be all though)
- Broadcast Connection: One-to-all
☐
2
a. Define the components of an ethernet frame
b. In a switch, what is the MAC address table?
c. Name and explain the process used to generate the MAC address table?
d. What are the benefits of using a switch over a hub?
e. Explain what makes up an ethernet MAC address
f. What is a spanning tree?
g. What is the purpose of a The Spanning Tree Protocol. Explain the algorithm and why it is used.
h. I covered two different situations where an Ethernet switch will broadcast a frame. Explain these two situations.
i. On a receiving machine, how would the protocol stack know that an Ethernet Frame contain an ARP request?
j. On a receiving machine, how would the protocol stack know that an Ethernet Frame contain an ICMP request?
k. Name and explain the algorithm used by a switch to prevent loops in the network.
Proof
a. An ethernet frame has:
Preamble: 7 bytes of alternating 0's and 1'sSFD: ... except for the last one which has double 1's on the last two bitsMAC Destination: 6 bytes of MAC address destination importantMAC Source: 6 bytes for MAC of source importanttype: Type (ex: DNS, TCP, ...) importantpayload: Data (variable number of bytes)CRC: checksumEnd of Stream Symbol: 12 bytes that represents the end of the stream
b. The mac address table is generated on a switch when a frame from a new device is sent. It looks at the sending MAC address and associates it with the switch it came from.
c. (see b)
d. A switch is a Multicast Connection device, while a hub is a Broadcast Connection device.
e. It's a 6 byte field
- The first 3 bytes identify the vendor (ex: Cisco, Netgear, ...)
- The last 3 bytes are a unique number within the vendor.
f. A spanning tree is any graph that doesn't have loops.
g. The Spanning Tree Protocol uses the spanning tree algorithm. Essentially, you do a BFS to find the shortest path between two nodes (ie: clients). If they have a loop (there is more than one path), then cut anything but the shortest path.
h. An ethernet switch will broadcast a frame when:
- It is forwarding traffic over the broadcast address with all
FF's - It is unknown what the MAC address of the sending device is, so it flushes the reference to the new MAC address in it's table.
i. In the type field it is the ARP type of value 0x0806
j. It sits at layer 3, not 2. It's a part of the IP protocol type field.
k. It uses the The Spanning Tree Protocol (see above).
☐
3
Regarding inter-symbol interference in multi-mode Fiber Optic Cable, explain what is inter-symbol interference and how modal dispersion can cause this in multi-mode Fiber.
Proof
It is the bleeding of bits into the next bit. Essentially, photons that move down the light tube will bounce at different speeds down the wire. When a high signal is set to low right after high (or vice versa), some of the straggling photons will start to come to the other end of the wire. This means that the wire is slowly loosing light, not nearly as instantaneously as that of a copper wire.
In multi-mode wire specifically, the glass tube is so big (the cladding is small), which is good since it's a cheaper way to make fiber-optic cable. However, it causes the photons to be more variant in their bouncing, creating inter-symbol interference. Instead, using single-mode fiber will help, as it has a smaller glass part and thus the variance is lowered. This increases costs, but also data speeds and distances.
☐
4
What is the difference between a logical and physical Network Topologies? Use examples.
Proof
Logical topologies describe the physical connections that are made between devices on a network (ex: copper ethernet wire). The network topology describes what connections are actually live or not, since often times we turn off cables (ie: remotely disconnect them) so we can influence their topology (for example, remove loops when doing The Spanning Tree Protocol).
☐
5
In the IEEE Standards (Ethernet and Wireless Standards) they break up the Data Link layer into two sublayers. Name the layers and explain why they broke the Data Link Layer into two parts.
Proof
The two layers are:
- Medium Access Control (MAC): deals with the physical layer, error correction (ie: using the ethernet preamble)
- Logical Link Control (LLC): frame assembly/disassembly and interfacing to higher levels
They broke this up so that the changing parts of the physical aspect of the Data Link layer can change over time, while protocols like TCP, IP (and UDP) Protocol Suite all still can work when interacting with the LLC.
☐
6
In socket programming, what information is needed to name a socket?
Proof
int socket(int domain, int type, int protocol);
// domain: AF_INET6
// type: SOCK_STREAM
// protocol: 0 (or can set to an agreed-on number)
☐
7
List the function calls in order on both the client and server needed setup and use a STREAMS based communication.
Proof
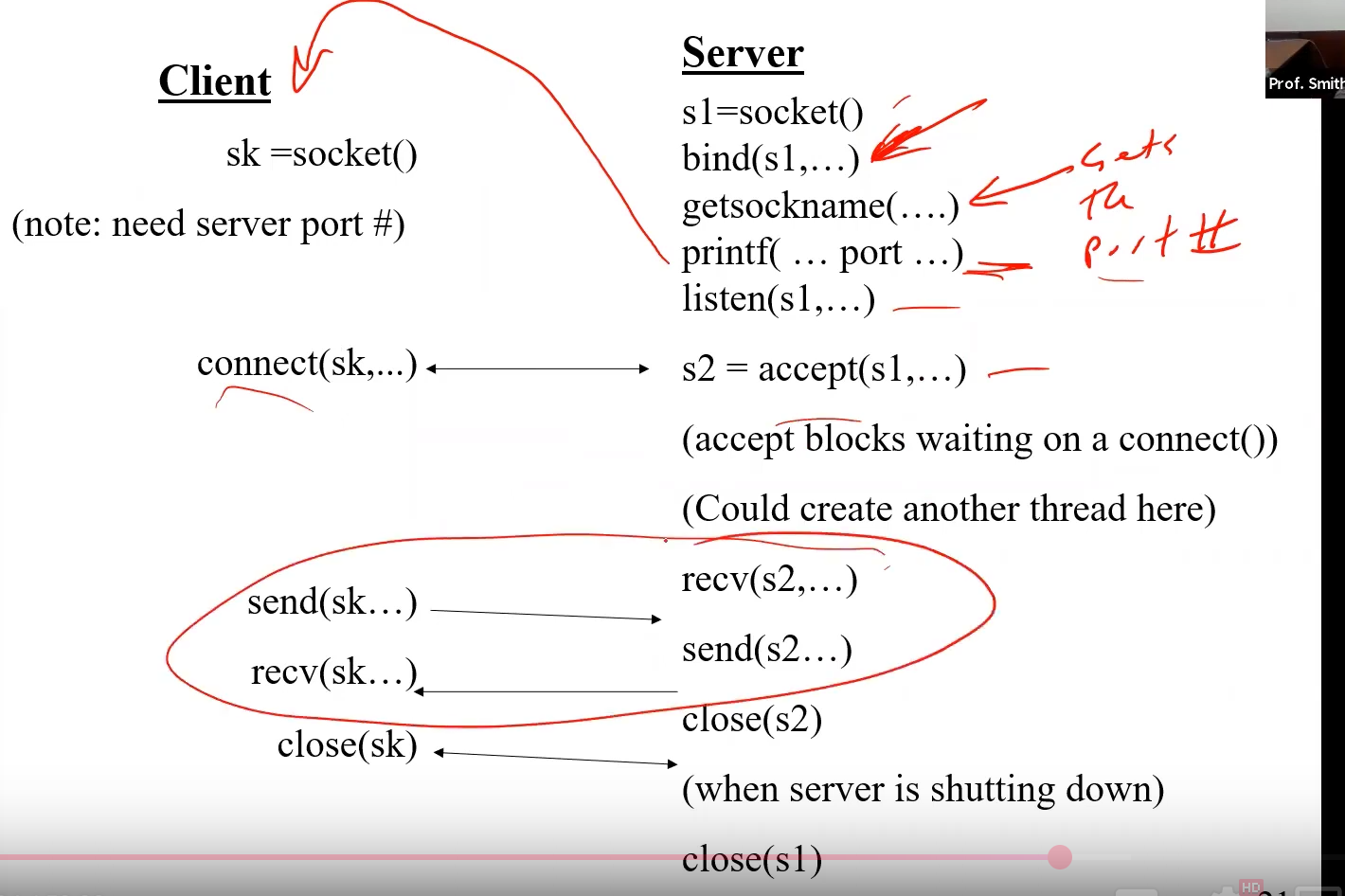
Essentially:
Setup:
- Both the server and client make a
socket() - The server
binds()the socket to somesockname()given by the user and agreed upon beforehand. Thenlisten()sets us up torecv()on that socket number. - The client will try to
connect()and the server will block onaccept()until a connection is made.
Use:
- The client will
send()any data it needs, while the server willrecv()it. - Repeat this ad nausium
Teardown:
- Close the socket numbers for the client and server
- The server has it's own socket number (since it made one for each connection, which we closed). Thus close that one too.
☐
8
A coding question: Dr. Smith says that calling the send() function is more “expensive” (takes more computer resources/will slow down your app more) then calling a function like strcpy(). Explain why he says this:
Proof
Calling send() requires much more IO resources, as the network has to handle sending that data (which could get lost, or may have a long travel time). This will use overall more resources.
On the other hand strcpy() will just copy data locally until hitting a \0 character.
☐
9

Proof
#include <string.h> // include memcpy()
#include <arpa/inet.h> // and endianness conversions
int createPDU(char * pduBuff, uint32_t pduBuffLen, char * payloadBuff, uint32_t payloadLen)
{
// Write the buffer header length
uint32_t pduBuffL = htonl(ntohl(pduBuffLen)+sizeof(uint32_t)); // conv. to host order, including header size
size_t i = 0;
if(memcpy(pduBuff, &pduBuffL, sizeof(uint32_t)) != pduBuff) return -1;
i += sizeof(uint32_t);
// Now write the payload data
pduBuff += sizeof(uint32_t);
if(memcpy(pduBuff, payloadBuff, payloadLen) != pduBuff) return -1;
return ntohl(pduBuffL);
}
☐
10
In a layered protocol stack, what does the term encapsulation refer to?
Proof
It describes how the lower layers include higher layer payloads with headers, but treat them just as payloads. Essentially, the whole layer 2 frame would have the layer 2, 3, 4, ... headers in order, then the inner payload, but only the layer of that application would know how to deal with that payload.
☐
11
Regarding the Internet Checksum:
a. What information/fields/data are covered by (included in) the IP checksum?
b. For the TCP checksum?
Proof
a. It includes the entirety of the IP header, taking in a pointer to it and the length of the IP header (which is constant usually, taken from the IHL field in the IP header)
b. It uses a pseudo_header as the first part of the buffer, then the actual TCP header afterwards. The pseudo header has:
- Src IP
- Dest IP
- Zeroes
- Protocol
- TCP Length
☐
12
How do you calculate the length of the IPv4 header?
Proof
You do 4 times the IHL value.
☐
13
How do you calculate the length of the TCP PDU?
Proof
You use the IPv4 header, which has the length of the whole payload, and subtract the IPv4 header part to get the total size of the TCP PDU.
☐
14
How does a router calculate the IPv6 header length excluding any option headers?
Proof
It is a constant 40 bytes without options.
☐
15
Regarding the internet checksum. If you receive an IP datagram with the correct checksum value in the IP header and run the checksum function across the IP header (without changing the checksum field), why do you receive a zero? Explain this based on how the Internet checksum works.
Proof
The checksum() function, at the very end, get's a hash value based on the values in your IPv4/6 header. At the very end it will return the hash value that it got minus the value in the checksum field of the header, which is not generated by the hashing algorithm. Thus, doing the subtraction gives 0, and is really just comparing if the checksum values are equal (0) or not (non-0).
☐
16
In two sentences, what is the Internet?
Proof
The internet is a bunch of clouds (really networks) where they all speak using the IP Protocol family.
☐
40
You are given the subnet mask of /22 and need to write it in the traditional dot-decimal notation (e.g. 255.xxxx.xxxx.xxxx). What is the dot-decimal notation for the /22 subnet mask?
Proof
It is 255.255.252.0.
☐