5 - IP Addressing
Recall from 3 Sockets Program, recv() and poll(), that:
bind()binds the IP address, port number, and type of connection (ie: TCP for our purposes)- How do you get the port number to the client? The server chooses whatever port number, then prints out the port number itself. Then when you run the client you pass it the IP address and this port number into
argvformain(). This is printed on the server viagetsockname()
IP Adressing
Today we'll talk about Protocol Layers, and namely routing across layer 3 is the focus of today.
In one word, IP addresses "route". IP Packets do this by Packet Switching using Routing Tables. The Internet tends to use this protocol to learn about the cloud that represents the network. This protocol generates this Routing Table.
To calculate the routing table:
- The Wireless Router active learns about the network
- It creates a list of the past IP addresses
- Search the Routing Table
- Forms the next packet by looking at the next hop (next IP is gotten from the routing table)
IP Header
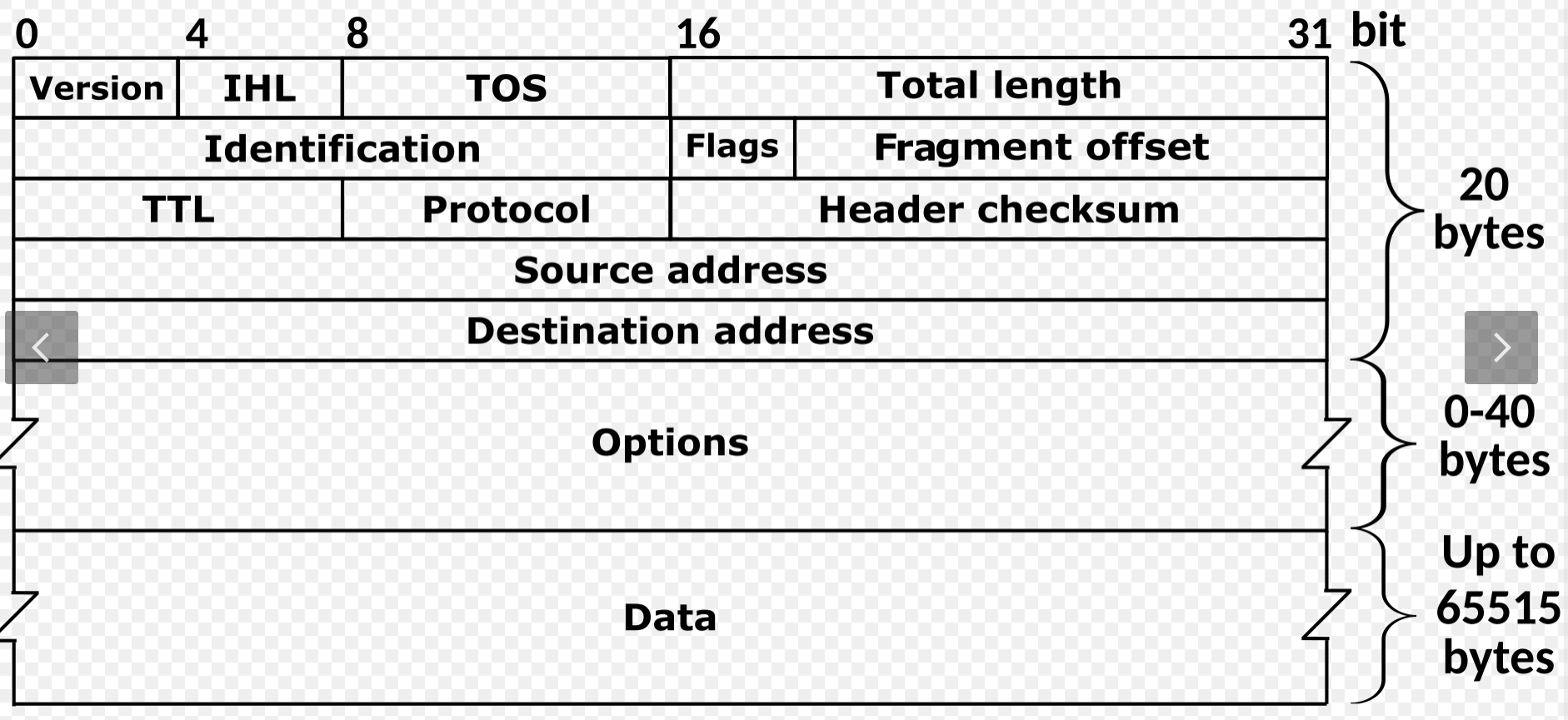
Here are some honorable mentions of what the bits mean:
TOS: Terms of Service.- First 3 bits depreciated.
- First 6-bit Differentiated Service bits (DiffServ)
- These bits called: Differentiated Services (DSCP)
- These are used to differentiate traffic from one to another.
- Each service (voice, video, data, ...) each have a DSCP number, so you check these bits to see what queue your packet is going to go to.
- These are all hardware cards, interfaced in our NIC - Network Interface Card OR Wireless Adapter
- Last two bits are explicit congestion notification bits
- These bits called: Differentiated Services (DSCP)
- Fragmentation and Reassembly (
Fragment Offset):- Recall that IEEE Standards (Ethernet and Wireless Standards) restrict ethernet to 1500 bytes (or some limit). Thus when we have a really large packet we need to break it up.
- Given a layer 4 TCP payload, the IP constructs the split by creating headers for each part:
- On the receiving side, how does we put the fragments back together?
- The
identificationbits before make sure fragmented IP dataframes identify with one another - The header on these have a
flagthat represent whether the traffic is fragmented (it stops at the last fragment). - The
fragment offsetfield says the number of bytes used, which must always be a multiple of 8 (we're in bytes), describing where in the PDU - Protocol Data Unit the payload starts at (ignoring the IP headers themselves)
- The
- Notice that because TCP traffic is only decoded on the start/end, then we keep it fragmented until we hit the destination.
- Time to Live:
TTL- Unlike in lab 2 Ethernet Switches that use The Spanning Tree Protocol, the internet is a vastly larger sea of devices (which takes forever).
- Everytime we hit a router, it decrements
TTLby 1. - Once it runs out, the router will kill the traffic (in case there is a loop, we want to kill the traffic to prevent infinite loops).
- Protocol: TCP, IP (and UDP) Protocol Suite
IPv4
We've already run out of IPv4 addresses, so now companies have to ask other companies for their addresses.
This is one reason why we are moving to IPv6.
Some properties about IPv4 address properties:
- IPv4 address is a 32-bit number (so ~4 billion unique addresses)
- Written in Dot Decimal Notation
1.23.34.56 - Each 8-bit number is an octet
- Address is hierarchial
- Global to local (the top bits are given to global networks like cal poly, and the lower bits are to specific devices like your computer)
- Ex: Cal Poly is
129.65.0.0 - My computer as of writing has IP
129.65.145.86
- Ex: Cal Poly is
- Think Zip code to street address
- Global to local (the top bits are given to global networks like cal poly, and the lower bits are to specific devices like your computer)
IPv4 numbers are organized by the Internet Assigned Numbers Authority. There's 5 regional registries:
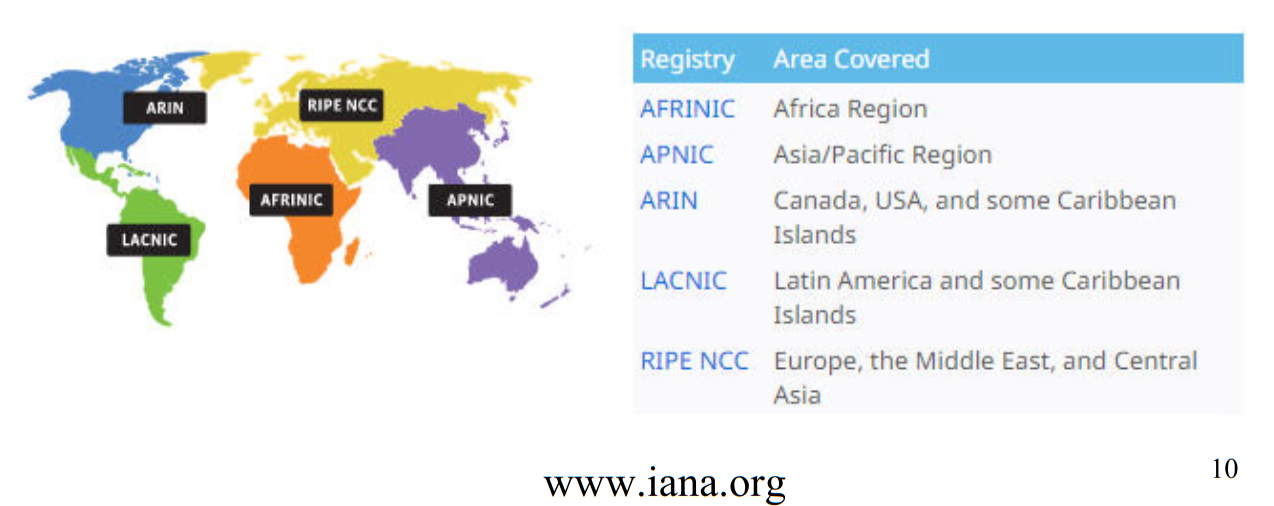
which organizes the global IP addresses (ie: the top bytes).
The IP address is broken into two parts:
- Network Part (
net-id):- This is the external IP of the network. (ex: Cal Poly)
- Host Part (local part of the address):
- Subnet: The top part of the lower half of the bits. This dictates the cloud of departments/regions we connect (ex: The CSC Department) and usually denote the address of a gateway (ie: a Wireless Router).
- Host: Device level bits (ex: your computer)
An Example of Hierarchical Network Addressing (used in IPv6)
The worry back in the day (and even now) is having too large of a Routing Table on the Internet. Each lookup requires a hash function operation, which over time adds up.
Say we're AT&T and this is our internet (as an ISP):
But what happens if we want to have different devices in a hierarchical fashion? If we have 4 children from our starting router, then we add 2 more identifier bits:
This process continues. Notice the /n notation, which dictates the subnet mask (ie: how many bits, from left to right, are valid and have to match).
This is called address agregation. When we route, we take note of which IP address subnets are in which directions:
Note that nowadays, because the top half of bits are given out, Cal Poly (and anyone with those higher bits) have way too many IP devices that they have to dole out. This is why this is moving into IPv6, and we are trying to put this into effect after the fact.
"The only way to know the slash is to ask" - Prof. Smith
Examples
Given 77.195.10.20/10, what is the network part of the mask?
- Answer: It's
77.192.0.0because we get 8 bits from the77part, then the top two bits of195 === 11000011giving us192. We may write this as77.192.0.0/10or77.192/10
Given44.89.130.89/20, what is the network part of the mask? - Answer: It's
44.89.128/20getting the higher 4 bits from 130
Here you can also just and the given subnet mask with the actual IP address:
77 .195 .10 .20 (Decimal Address)
01001101.11000011.00001010.00010100 (IP)
11111111.11000000.00000000.00000000 (Subnet Mask)
-----------------------------------
01001101.11000000.00000000.00000000
77 .192 .0 .0
Given someone has a 130.170.168.159/18 subnet mask, if they want to give out a 2nd tier netmask with /22 then:
- They can have 16 2nd tier networks
- The IP address above becomes on the 2nd tier subnet
130.170.168.0/22
Given a subnet mask of /25 using this 2nd tier subnet mask then:
- There's 8 3rd tier subnets possible
- The subnet part would be
130.170.168.128/25
A lot of devices don't know where to put the /n part of the subnet, so instead they use the dot decimal format, where the mask is actually given as a decimal number:
11111111.11111111.11111111.10000000/25 (Subnet Mask)
255 .255 .255 .128 (Dot Decimal)
You'll need to be able to actually break out the bits of just the host. For example, for the IP address 130.170.168.159/25 then:
- The host is
0.0.0.31 - It's on the
130.170.168.128/25subnet
You have to say it like this, since really you are saying what your IP is (and that's a redundant question).
For the number of hosts, just look at the remaining bits for the host, and subtract 2. For example, on 65.33.18.10/26 then we have:
The reason is that we have 2 invalid addresses this way, all 0's and all 1's. Thus we get rid of them.
Site Local Addresses
Some addresses are site local, for example 192.168.0.0, which never leave your house. Essentially, the Wireless Router you have only has outgoing IP information, so then your router can be treated as a device, and just coagulate all the outgoing requests and handle it.
Note that localhost, or 127.0.0.1 is the same machine as yourself.
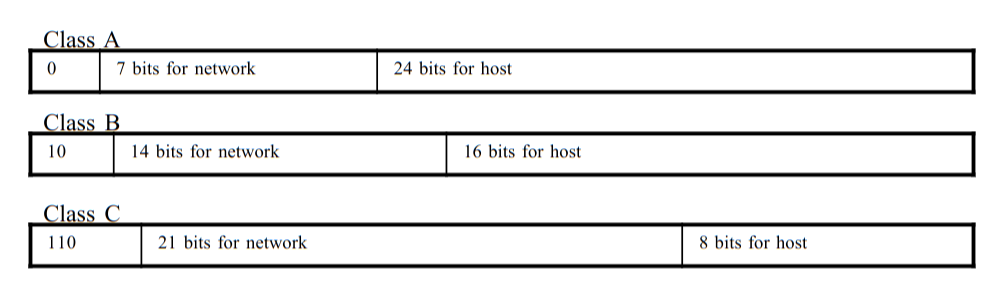
Classfull IP Addresses
This is an older addressing scheme, where they were broken up into 3 classes (rather than our subnet divisions):
/8: Class A/16: Class B/24: Class C
So you couldn't be an ISP and only offer /22 subnets. The issue with this is that then people initially were able to have a ridiculous amount of hosts.
MIT for example had a Class A, and thus had /16 so then they got considerably less, but still more than enough.
Having a class C is much more sustainable for say a college, since then there's likely going to be enough router traffic that it can handle all the traffic for new devices.
Routing Table Considerations
You would think that the Routing Table can be quite small, but over time there has been a sigmoid increase in table:
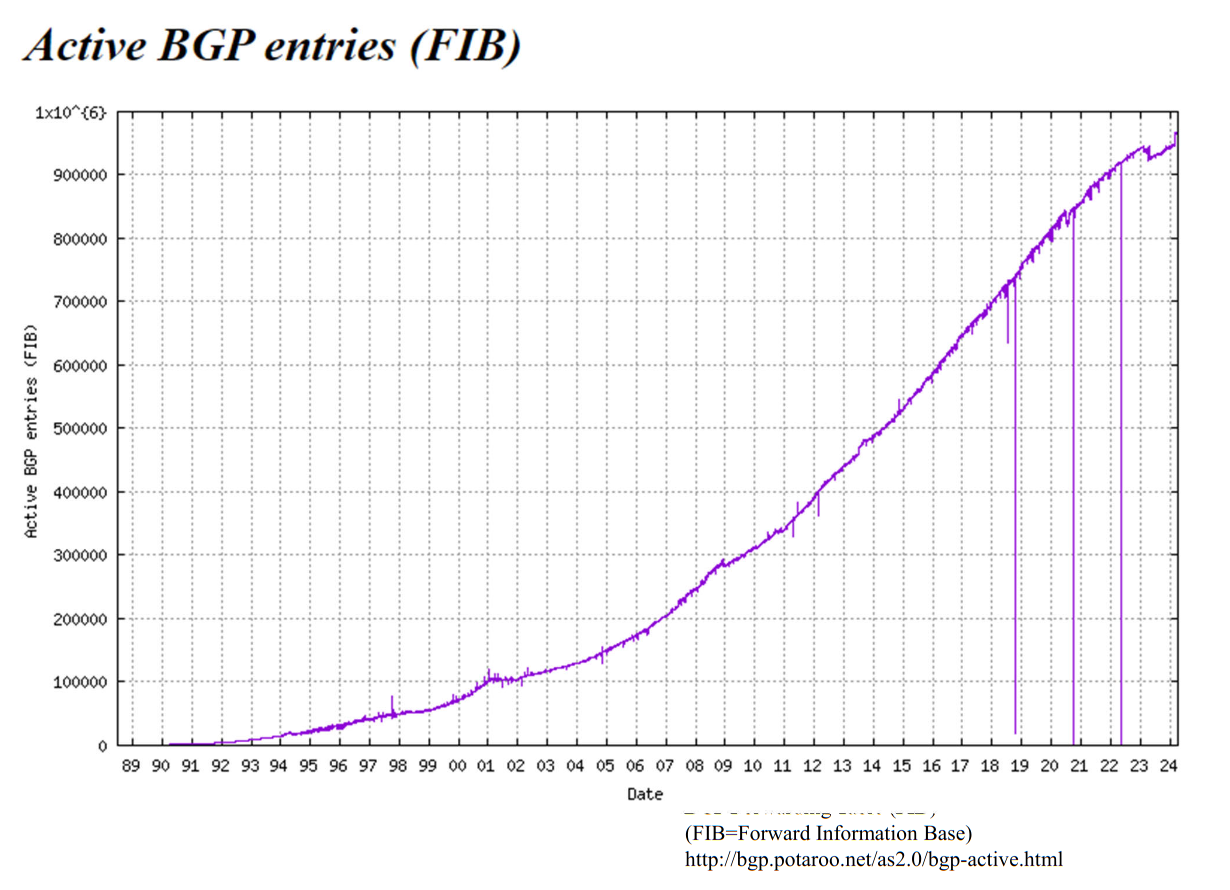
(note: these are for the core routers handled via ISPs)