10 - IPv6, Tunneling
Reminders:
- You can bring a notecard (3inx5in) (please do lol)
- Go to your section.
- Last lab final questions are due next Wednesday (so don't stress)
- Review session at 6 today.
- For the MT assume default gateways exist at the "head" of the subnet when not mentioned.
Again, all you really need to ask is:
"Are the two devices on the same subnet" - Prof. Smith
You must know yes/no before doing anything.
IPv6
Unlike IP Addressing (IP Protocol) with IPv4, all that changes is the size of the address space. It is:
- 16 byte (128 bit) address space (compared to 32 bit IPv4)
- Shorten the header to only 8 fields - adding more options as needed
- Better support for options
- Authentication and Security (this one kinda fizzled out)
- Options for types of services were improved
- Got rid of the checksum (the error rate over wire is already very small, which can be handled by TCP instead)
The thing is that any of these problems (other than address space) already had a solution in IPv4, so really there's more cost to developments using IPv6 than IPv4.
History
We didn't have any problems using IP Addressing (IP Protocol) with IPv4 until pretty recently. Why would Amazon support IPv6 if the clients can't support it (or vice versa)? Both need to support the protocol for the thing to work.
That is until now, where after solving the chicken-and-egg problem we finally have servers and clients that support the protocol. The big tug was the number of IP addresses are running out, so we can use this protocol to make more where needed.
Header
See the header below:
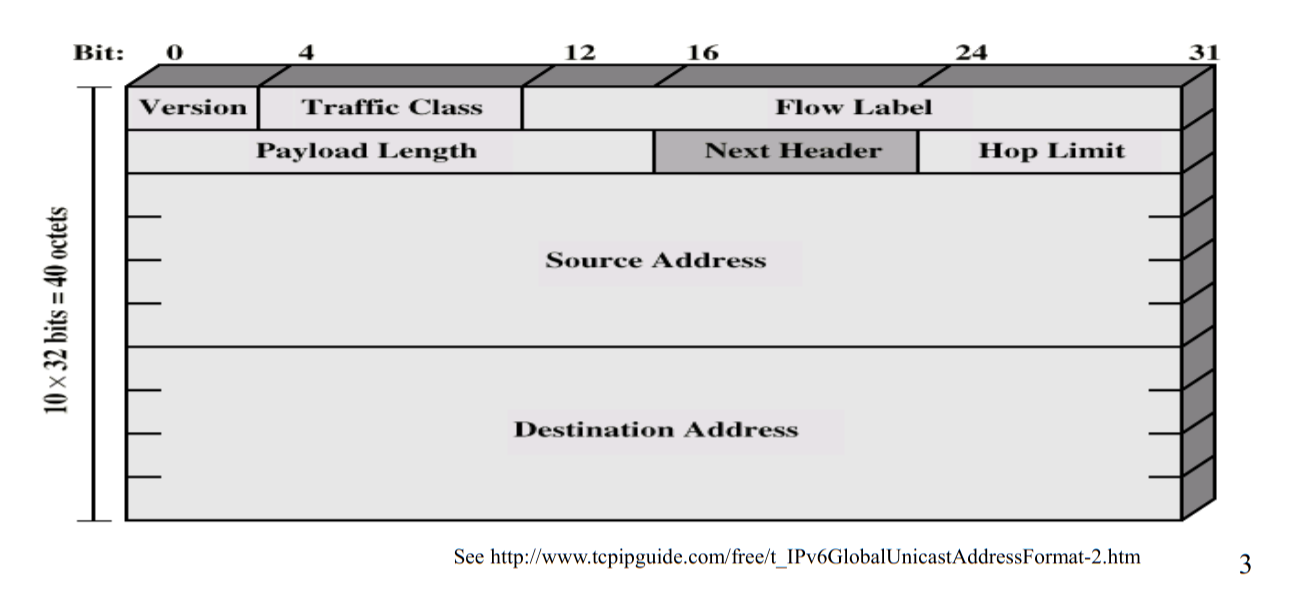
Going through it:
version: Is 6 in this case (for IPv6)traffic_class: is TOS (see IPv4)flow_label: is a WIP (they don't really use it anymore, and if they do it's not a standard)payload_length: length of the payload after the headernext_header: whether we end reading new headers as IPv6 or nothop_limit: TTL essentially.
What's missing? No fragmentation header! The router is going to get a PDU - Protocol Data Unit and if it is too large it throws it away. Fragmentation and assembly only happen at the source/destination.
There are extension headers that are optional for the header. These are always some variable headers, described below:
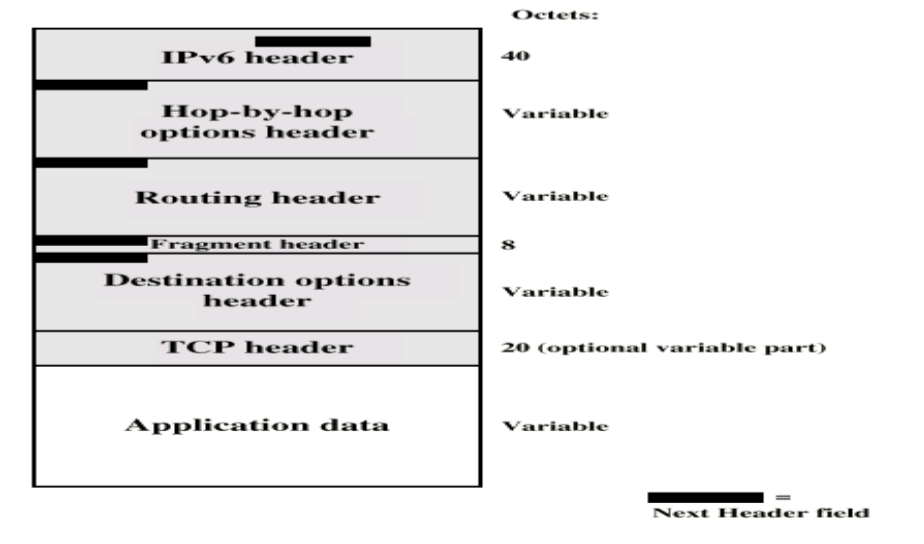
Some notes:
- IPv6 header is used by the source/destination
- TCP header used by source/destination
- Everything else pretty much is used by the routers in between.
authenticationheader is used by the routers in between to encrypt/decrypt traffic. This is called IPSec, short for IP security
Types of Addressing
We have three types, Unicast Connection, Multicast Connection, and Anycast. This is one-to-one of a set, meaning if you have a set of servers/devices and you want to send to one of those. It's up to Google to figure out how the traffic gets routed internally, while the client only cares about the connection to get to Google (really the routers do but yeah).
The idea is, before DNS, the routers in between would tell your device where the closest server to say Google is, and then you'd use that IP address to send it there (Google handles the rest).
IPv6 doesn't have Broadcast Connection
The address itself looks like 4 hex numbers, for 8 sets:
89AB:0000:0000:0000:1123:0067:89AB:CDEF
(can also remove leading zeroes using ::)
89AB: : :1123:67 :89AB:CDEF (read from Left to Right)
The idea is the IPv6 information will be passed to the host via a process similar to DHCP.
IPv6 Addressing
The way they are allocating these addresses now is that:
- 3 bits - format prefix (001)
- 13 bits - Top level IP ID (TLA-ID) (from your ISP most likely)
- 8 bits - reserved
- 24 bits - NLA-ID (can be from various companies, ex: Cal Poly)
- 16 bits - SLA-ID (from the subnet, so then we have
- 64 bits - Interface ID (host ID, your MAC address)
for a total of 128 bits.
Privacy and Security Issues
The network interface identifier (MAC) is unique to a device - no matter where you move. Using IPv6 would:
- make it easier for someone to guess your IP
- makes it easy for someone to track your movements
since they just have to correlate your interface ID.
Instead, some devices will randomize the last 64 bits (ie: the interface ID) and give temporary IDs so that when you do move the ID has been used and any new one would be uncorrelated to the old one.
NAT
NATv6 (at least they would rather you not NAT IPv6) was an edge protocol such that the router at your house would translate a local IP address (such as 192.168.0.1) to an external (your router's) IP address.
Note that NAT can break SIP (used for Voice over IP). There's also privacy extensions for IPv6 like Stateless Address Autoconfiguration (SLAAC).
Essentially for each part between IPv6 and IPv4, we add/remove the IPv6 header between networks that support one protocol or the other.
The reason this works is that the address is "spoofed" in that the header information is obfuscated when we go from IPv6 to IPv4, and vice versa. The devices at the interims have to "make" addresses on the fly so they can send the traffic over the network.
VPNs (virtual private networks) will actually just make an encrypted header that decodes the payload, then all the traffic over the network will not be able to read it, until it reaches the client who can decode the encryption.
This is in contrast to translation, where the header itself has to be converted one-for-one, rather than be included in the payload:
Some solutions do this and force intermediate routers to support both. DNS servers translate between both IPv4 and IPv6 (they give you 4 if you support 4, or 6 if they support 6. If the server supports only the 4 address it'll give you that).